How to Secure Vicidial servers asterisk/mysql/apache
A complete guide to secure the vicidial or hardening the vicidial based dialers. The vicidial based dialers like vicibox , Goautodial or vicidial scratch installs have so many loop holes or vulnerabilities which pays way to hack the server. The vicidial is a bundle of Asterisk, MySQL/MariaDB , Apache , Astguiclient and Linux OS, you need to secure each on these software's and OS to secure the entire vicidial Dialer. In this article i have provided the ways to secure these software's with respect to vicidial operation.

|
| how to secure vicidial |
Vicidial Security -What is Vicidial?
In this Blog i will be showing you few Tips to Harden or Securing the Vicidial.
Note: though its not 100%, but i covered all security flaws I come across.
if you have found which is not listed here, kindly post in comment.
Vicidial Major Components
Below are the list of Major Software's used in Vicidial Setup,
we will see hardening of each components related to vicidial , for in-depth hardening there are so many websites to refer like tecmint.com,geekflare.com,tecadmin.net etc.
Mysql/MariaDB - Database
Asterisk - Telephony Software
Apache - Webserver
Linux - Operating Systems
Astguiclient - Vicidial software
1. Mysql/MariaDB (DATABASE)
MySQL is an open-source relational database management system (RDBMS),
MariaDB is a fork of the MySQL database management system.
Vicidial use either mysql or mariadb as there default database software.
Below are the list of Security enhancement for the Vicidial Database.
1.1 : Vicibox Mysql Root Password.
If you are the one who using the Vicibox Installer to install vicidial, you may notice the default Root password of Mysql/mariadb is No Password(empty) ie: without password you can login to mysql with root user.
Though the root remote login is disabled ,but best practice is to set password .
To set the root password follow the below steps.
run mysql_secure_installation command ,which prompt you to set password and other usefull settings like Remove anonymous users, Disallow root login remotely etc.
mysql_secure_installation
Enter current password for root (enter for none):
Change the root password? [Y/n] Y
New password:
Re-enter new password:
Remove anonymous users? [Y/n] Y
Disallow root login remotely? [Y/n] Y
Remove test database and access to it? [Y/n] Y
Reload privilege tables now? [Y/n] Y
1.2: Vicibox Mysql BIND-ADDRESS
If you don’t need to access your database from another machine it is suggested to bind MySQL service on localhost only, edit the configuration file my.cnf and set bind-address:
By default it is set to 0.0.0.0 ,that is listening on all Interface attached to the server.
vi /etc/my.cnf
under [mysqld] context set bind address
bind-address = 127.0.0.1
[mysqld]
bind-address = 127.0.0.1
restart mysql
systemctl restart mysqld
Note: this will not applicable for Vicidial Cluster setup , in cluster use dedicated interface ip which is not connected to public or use iptables to restrict the ip's
1.3 : Vicidial Mysql Default Users
The Default username and password used by vicidial to interact with database are
1. cron - password 1234
2. custom - password custom1234
Its Best practice to delete the default usernames/passwords and user your own usernames with complex password.
Command to delete the default vicidial mysql users
login to your mysql using root credentials
mysql -p
mysql>DROP USER 'cron'@'localhost';
mysql>DROP USER 'custom'@'localhost';
Now lets create our own usernames with complex password, for
demonstration i used, myxyz and customxyz but recommend you to use your
own usernames, which is not easy guess.
Command to create new mysql user
mysql>CREATE USER 'myxyz'@'localhost' IDENTIFIED BY 'newpassword';
mysql>CREATE USER 'customxyz'@'localhost' IDENTIFIED BY 'newpassword';
Next we need to grant the permission to new users for the database
asterisk,
(note: asterisk is default database used by vicidial).
GRANT SELECT,INSERT,UPDATE,DELETE,LOCK TABLES on asterisk.* TO myxyz@'%' IDENTIFIED BY 'newpassword';
GRANT SELECT,INSERT,UPDATE,DELETE,LOCK TABLES on asterisk.* TO customxyz@'%' IDENTIFIED BY 'newpassword';
GRANT SELECT,INSERT,UPDATE,DELETE,LOCK TABLES on asterisk.* TO myxyz@localhost IDENTIFIED BY 'newpassword';
GRANT SELECT,INSERT,UPDATE,DELETE,LOCK TABLES on asterisk.* TO customxyz@localhost IDENTIFIED BY 'newpassword';
GRANT RELOAD ON *.* TO myxyz@'%';
GRANT RELOAD ON *.* TO myxyz@localhost;
GRANT RELOAD ON *.* TO customxyz@'%';
GRANT RELOAD ON *.* TO customxyz@localhost;
flush privileges;
Finally update new mysql user details in vicidial conf file
astguiclient.conf located in /etc/
vi /etc/astguiclient.conf
update the below details
VARDB_user => myxyz
VARDB_pass => myxyzpassword
VARDB_custom_user => customxyz
VARDB_custom_pass => customxyzpassword
1.4 : Vicidial Mysql Default User Password
If you dont want to create new users or delete existing users as mentioned in 1.3, but just to change the default users password, follow this steps, if not skip for next section
mysql command to change the password of users cron and custom
ALTER USER 'cron'@'localhost' IDENTIFIED BY 'newpassword';
ALTER USER 'custom'@'localhost' IDENTIFIED BY 'newpassword';
flush privileges;
once Password changed update the vicidial conf file astguiclient.conf
vi /etc/astguiclient.conf
edit the blow details
VARDB_pass => new-cron-password
VARDB_custom_pass => new-custom-password
1.4 : Vicidial Mysql Default Database Name - asterisk
The default Database name used in vicidial is "asterisk".
which is well known name and documented
in vicidial manual, so its easy cake for hackers to exploit once they have
access to your server and database. Its best practice not to use the
default mysql database names.
Steps to change the default database name.
I personally recommend to take backup of the current asterisk database and restore the backup to a newly created database,
Step1 : Backup the asterisk DB
cd /usr/src/mysqldump -p asterisk > asterisk.sql
Step 2: Create new Database eg:abcxyzdb
mysql -p
mysql>CREATE DATABASE 'abcxyzdb' DEFAULT CHARACTER SET utf8 COLLATE utf8_unicode_ci;
Step 3: Grant necessary permission to mysql users to new db strikerdb
note: if you are using cron/custom user then run below commands, or replace cron/custom to the username created in mysql.
GRANT SELECT,INSERT,UPDATE,DELETE,LOCK TABLES on abcxyzdb.* TO cron@'%' IDENTIFIED BY '1234';
GRANT SELECT,INSERT,UPDATE,DELETE,LOCK TABLES on abcxyzdb.* TO custom@'%' IDENTIFIED BY 'custom1234';
GRANT SELECT,INSERT,UPDATE,DELETE,LOCK TABLES on abcxyzdb.* TO cron@localhost IDENTIFIED BY '1234';
GRANT SELECT,INSERT,UPDATE,DELETE,LOCK TABLES on abcxyzdb.* TO custom@localhost IDENTIFIED BY 'custom1234';
flush privileges;
Step 4: Restore the asterisk db backup to new database.
cd /usr/src/
mysqldump -p abcxyzdb < asterisk.sql
Step 5: update the astguiclient.conf file
vi /etc/astguiclient.conf
# Datavase connection information
VARDB_database => abxyzdb
Step 6: Delete the default database
mysql -pDROP database asterisk
2. Asterisk- Communication software
Asterisk is a Open source Communication software , You can use Asterisk to build communications applications, things like business phone systems (also known as IP PBXs), call distributors, VoIP gateways and conference bridges.
Vicidial uses asterisk as communication software for sip trunking, Conference bridged module for there agent sessions ,SIP,IAX ,webrtc for end user phones, and utilizes many features of asterisk.
Lets See Few Tips to secure the Asterisk which is installed in Vicidial Setup's.
2.1- AMI Default Users and Passwords.
Vicidial uses AMI (Asterisk Manager Interface ) to interact with asterisk for call origination, termination, update etc. with predefined username and password.
Anyone who is having these credentials can remotely originate ,terminate or send asterisk commands.
The Best Practice recommended to change these default usernames and update the same in Vicidial ADMIN-SERVER settings.
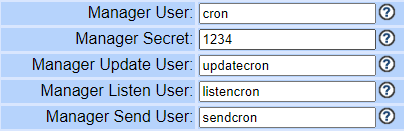
The default AMI usernames are
1. cron
2.updatecron
3. listencron
4. sendcron
All these users have common password of 1234.
Steps to Change the default AMI users.
STEP 1: rename the AMI user in the manager.conf file
vi /etc/asterisk/manager.conf
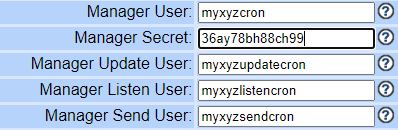
rename the default users and passwords ,rename it to something which is not easy guess.
for demo purpose i used myxyz before all the usernames with common password of 36ay78bh88ch99.
[myxyzcron]
secret = 36ay78bh88ch99
read = system,call,log,verbose,command,agent,user,originate
write = system,call,log,verbose,command,agent,user,originate
[myxyzupdatecron]
secret = 36ay78bh88ch99
read = command,reporting
write = command,reporting
[myxyzlistencron]
secret = 36ay78bh88ch99
read = system,call,log,verbose,command,agent,user,dtmf
write = command
[myxyzsendcron]
secret = 36ay78bh88ch99
read = command
write = system,call,log,verbose,command,agent,user,originate
STEP 2: Update the New AMI users in Vicidial Server settings.
Login to your vicidial admin portal ,
Navigate to server settings
ADMIN > SERVERS,
update the below fields with our new AMI users and press submit.
My updated AMI details in SERVERS.
2.2- AMI BIND ADDRESS
By default asterisk manager bind address in vicidial setup is set to 0.0.0.0 , which means listen to all the interface attached to the server.
If you are using single server vicidial setup, or to restrict AMI connection remotely, restrict this to the local host or the internal interface ip.
vi /etc/asterisk/manager.conf
bindaddr = 127.0.0.1
save the file and reload asterisk once
asterisk -rx "reload"
2.3- AMI ACL Restriction.
By default AMI users are no restricted to specific ip or subnet in vicidial.
if you have restricted the AMIN bind address to 127.0.0.1 then you can discard this options or if you have a cluster setup you can proceed with these steps to restrict the AMI users to specific ip and subnets or multiple ip's.
For every AMI add the deny and permit options similar to below .
Restricting to local host only
[cron]
secret = 1234
read = system,call,log,verbose,command,agent,user,originate
write = system,call,log,verbose,command,agent,user,originate
deny = 0.0.0.0/0.0.0.0
permit = 127.0.0.1
Restricting to a subnet
[cron]
secret = 1234
read = system,call,log,verbose,command,agent,user,originate
write = system,call,log,verbose,command,agent,user,originate
deny = 0.0.0.0/0.0.0.0
permit = 192.168.1.0/255.255.255.0
Restricting to multiple ip's/ subnet
[cron]
secret = 1234
read = system,call,log,verbose,command,agent,user,originate
write = system,call,log,verbose,command,agent,user,originate
deny = 0.0.0.0/0.0.0.0
permit = 127.0.0.1,10.10.10.10,192.168.1.0/255.255.255.0
2.3- Asterisk Default IAX peers.
By default vicidial will create three IAX peers , which are used by vicidial for blind transfer and monitoring purpose.
The iax peers are
1. ASTloop
2. ASTblind
3. ASTplay
Although these iax peers are protected with strong password ,which is generated in initial installation of vicidial, but still open to public for registration that is: bind to any IP.
Securing IAX Peers:
Option 1: bind address
If you are using single Single server setup, and not using any IAX softphones extensions then restrict the IAX bind address to 127.0.0.1
vi /etc/asterisk/iax.conf
bindaddr=127.0.0.1
Option 2: ACL -deny/permit
If you are using cluster setup or any iax softphone extensions, restrict the registration to particular ip or subnet or list of ip's using deny and permit option as show below
[ASTloop]
accountcode=ASTloop
secret=60JMuzlTg0bksLu
type=friend
requirecalltoken=no
context=default
auth=plaintext
host=dynamic
deny=0.0.0.0/0.0.0.0
permit=127.0.0.1,192.168.0.0/255.255.0.0
Note : these IAX peers are autogenerated by Vicidail scripts, any manual modification will be erased in next reboot or while running rebuild conf in server settings.
$Liax .= "\n";$Liax .= "[ASTloop]\n";$Liax .= "accountcode=ASTloop\n";$Liax .= "secret=$self_conf_secret\n";$Liax .= "type=friend\n";$Liax .= "requirecalltoken=no\n";$Liax .= "context=default\n";$Liax .= "auth=plaintext\n";$Liax .= "host=dynamic\n";$Liax .= "deny=0.0.0.0/0.0.0.0\n";$Liax .= "permit=127.0.0.1,192.168.0.0/255.255.0.0\n";$Liax .= "disallow=all\n";$Liax .= "allow=ulaw\n";if ($conf_qualify =~ /Y/){$Liax .= "qualify=yes\n";}
2.4- Asterisk Default SIP Peers- gs102
By default vicdial installation will be updated with default sip peer by the name gs102.
which is marked as test admin phone.
though the latest vicidial installations initial setup force to set a strong password ,but still its a easy guess for the available sip peer in system, its better to delete this peer.
ADMIN > PHONES > gs102 > delete this phones
2.5 - Securing the SIP Phones with ACL template.
By default sip phones created in vicidial will have the default sip settings, like host = dynamic,
without any ACL restriction ,no call-limit .
Its better to create sip phones with Proper ACL and any other sip security settings like call-limit
Additional sip settings can be achieved by creating a SIP template in vicidial with below settings and attach to the phones created in vicidial
ADMIN > Templates.
type=friend
disallow=all
allow=ulaw,g729
deny=0.0.0.0/.0.0.0.0
permit=192.168.0.0/255.255.0.0,10.10.0.0/255.255.0.0
call-limit=1
Note: Always use STRONG Registration Password.
3. APACHE - Webserver
Apache HTTP Server is a free and open-source web server that delivers web content through the internet. It is commonly referred to as Apache and after development, it quickly became the most popular HTTP client on the web.
Vicidial uses Apache as its webserver to deliver its web content that
is
vicidial admin and agent portal.
In this blog i am going to list out few hardening related to vicidial,
There are so many blogs available in internet for complete apache
hardening/security.
3.1: Disabling the Directory listing
By default Apache list all the content of Document root directory in the
absence of index file.
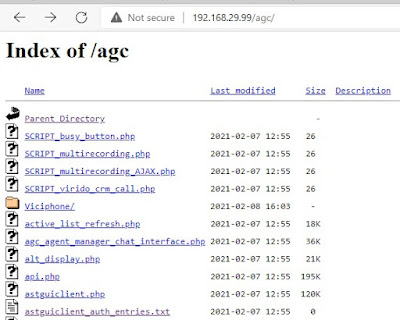
As you may notice by browsing the vicidial webfolders you can see all the
folders and files within the vicidial and Agc webfolders as show
below
https://vicidial_ip/vicidial/ orhttps://vicidial_ip/agc/
In both the folders ,you might notice a file named
"project_auth_entries.txt"
by opening this file you can see all the failed logins, with IP address of
both local and public ip's.
Also the file vicidial_auth_entries.txt under agc
folder list the successful user logins .this will given the hackers the hint of usernames used in the
vicidial servers, these user attempts logs should be stopped along.
Below are the steps to disable the Directory listing and Stopping the
user attempts logs in files under web folders..
Steps to Disabling the Directory Listing.
We can turn off directory listing by using Options directive(-Indexes) in
http configuration file .
If you are using Vicibox follow the below steps
cd /etc/apache2/conf.d/
vi 1111-default-ssl.confandvi 1111-default.conf
Options -Indexes +FollowSymlinks
Note: for Scratch install in centos just edit the file httpd.conf under /etc/httpd/conf/
save the file and restart the apache or httpd
systemctl restart apache2
Followed to that now access the webfolders vicdial and agc ,you should get permission denied as shown below
For vicibox
cd /etc/apache2/conf.d/
vi vicirecord.conf
Replace the below line
Options Indexes Multiviewsave and restart the apache
TO
Options -Indexes +FollowSymLinks
systemctl restart apache2orsystemctl restart httpd
3.2 Steps to disable the logging of failed details
Step 1: Log in to your vicidail admin portal
http://fqdn/vicidial/admin.php
Step 2: Navigate to ADMIN > SYSTEM SETTINGS
Step 3: Disable Webroot Writable that is: set it to 0
Step 4: submit
this will disable the logging of failed and sucessful login attempts in files under web folders.
3.3: Securing Vicidial Recording Folder
I have a separate post for securing the vicidial recordings folder , refer it for vicidial recordings security.
3.4 -- Vicidial web Path Default Names
By default the web paths for the Vicidial Admin, Agent , Recording portals are
http://FQDN/vicidial/http://FQDN/agc/http://FQDN/RECORDINGS/
These paths are default names and well known for hackers.
for best practice change the path either prepending a folder or
change the entire name.
Example:http://FQDN/abcxyz/vicidial/admin.phphttp://FQDN/abcxyz/agc/vicidial/phphttp://FQDN/abcxyz/RECORDINGS/
cd /srv/www/htdocs/mkdir abcxyzmv vicidial abcxyzmv agc abcxyzmv chat_customer abcxyzrm -rf index.html
http://FQDN/abcxyz/vicidial/admin.phphttp://FQDN/abcxyz/agc/vicidial.php
Note:For Recordings Path refer my article mentioned in above topic 3.3
3.5 :Vicidial PHPMYADMIN
STEPS to ACL
cd /etc/apache2/conf.d/cp phpMyAdmin.conf.rpmsave phpMyAdmin.confvi phpMyAdmin.conf
Require ipaddress (ie Require 11.12.13.14)
save the file
restart apache
Note: by default 192.168.0.0/16,10.0.0.0/8,172.16.0.0/12 subnet is
added in allow list
4. Vicidial - Astguiclient
VICIdial is an enterprise class, open source, contact center suite in use
by many large call centers around the world.
With Respect to vicidial below are the list of Security concern
to be addressed.
4.1 Default Admin User 6666
By default the vicidial comes with
admin username as 6666, which is well know username.
For best Practice create a new admin user with Strong Password and
delete the 6666 user.
4.2:Default Users
By default in Vicidial below user are created.
VDCLThough these users are in inactive mode, but these users use the password as donotedit.
VDAD
for best practice change this password to a strong password.
4.3:Use User Password encryption
By default in vicidial the user passwords are in plain text, which
means other admin user can see your password.
Vicidial have the option to enable password encryption, Refer my article Vicidial user password encryption to encrypt the passwords
4.4:Enable Two Factor authentication for admin
Vicidial have included the Two factor authentication for admin portal
access.
soon i will post the step by step guide here. You can refer the vicidial official document
4.5:Auto Deactivate the inactive users.
Vicidial have inbuilt Container settings to De-active the users who are inactive for N number of days.
4.6:Password Stuff.
Enable the below settings and set a strong password
ADMIN > SYSTEM SETTINGS
User Password Minimum Length
Default Phone Registration password
Default Phone Login Password
Default Server Password
4.7:Vicidial user level
Make use of user levels in vicidial, assign the levels according to there Role in accessing the vicidial
Level 1-6 - Agents/Closer/Remote Agents
Level 7 - Reports View Only User
Level 8 - ADMIN – Can’t edit Level 9 Users
Level 9 - Super ADMIN
also Use the option
Modify Same user Level
Alter Admin Interface Options
4.8:Agent Screen Logout Link Credentials
By default in Vicidial , the Agent credentials are linked to URL and saved in Browser history once they press logout as show below.
https://192.168.29.99/agc/vicidial.php?relogin=YES&session_epoch=1642271230&session_id=8600051&session_name=1642271228_100117849463&VD_login=1001&VD_campaign=TEST&phone_login=1001&phone_pass=1001&VD_pass=1001&LOGINvarONE=&LOGINvarTWO=&LOGINvarTHREE=&LOGINvarFOUR=&LOGINvarFIVE=&hide_relogin_fields=
ADMIN > SYSTEM SETTINGS
Agent Screen Logout Link Credentials - set this to 0
5.Linux - OS
Vicidial will support most the linux distributions like centos, ubuntu, rocky, opensuse.
with respect to vicidial operation, the major security concern related to OS level is the SSH access, which are open to public and needed to access the dialer for daily operation.
SSH : Below few security tips to secure SSH access.
1. Change the Default port 22 to something 2222, 23232 etc.
Though changing the port will not stop the attack but it will reduce the attack.
2. Apart from Root user ,create additional users with strong password, and disable the root login via SSH and use sudo or su options to access dialer with root permission.
to disable the root login via ssh edit
sshd_config file, and set the below line
PermitRootLogin no
3. Enable the brute force protection to block the IP who attempted with failed login credentials
Refer my article on vicidial SSH Bruteforce protection
4. Use Firewall, IPtables, vicibox Dynamic Portal.
Use IPtables to allow and deny the IP's or Ports which are needed to access the server.
Major Ports used in vicidial
5060(UDP) - SIP Protocol
4569(UDP) - IAX Protocol
5038(TCP) - AMI
1000-20000(UDP) - RTP Ports
8089(TCP) - webphone
80/443(TCP) - HTTP
5060(TCP) - mysql/mariadb
22(TCP) - SSH
Sample Iptables
iptables -A INPUT -s 127.0.0.1 -j ACCEPTiptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPTiptables -A INPUT -s 11.11.11.11 -j ACCEPTiptables -A INPUT -p tcp --dport 22 -j ACCEPTiptables -A INPUT -p all -j DROP
Conclusion:
Hope with the help of this article you have secured your vicidial servers, apart from these option you can use the vicidial Dynamic portal to allow access to agents and admin's who are authenticated with portal to add there IP in whitelist






How to secure vicidial,
how to secure vicibox
how to secure goautodial
Hardening vicidial
securing vicidial.
Thank you